Protocols
Introduction
- When communicating over networks, it is essential that some form of protocol is used by the sender and receiver of the data.
- Both parties need to agree the protocol being used to ensure successful communication takes place.
TCP/IP protocols
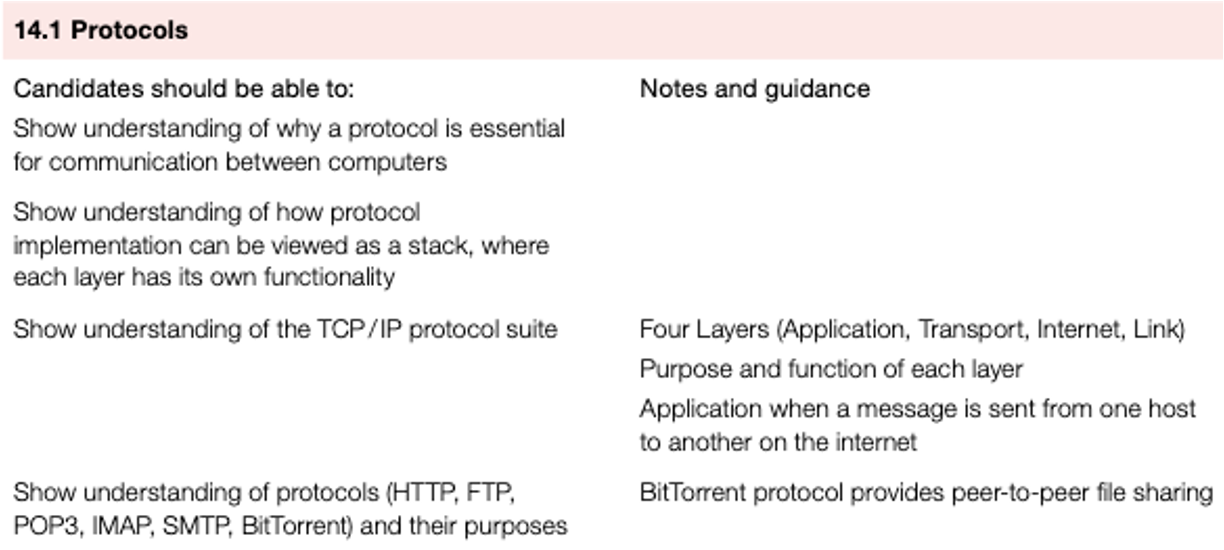
- This is the four-layer structure for TCP/IP protocols:
Application layer
- The application layer contains all the programs that exchange data, such as web browsers or server software; it sends files to the transport layer.
- This layer allows applications to access the services used in other layers and also defines the protocols that any app uses to allow the exchange of data.
| col1 | col2 |
|---|---|
| HTTP | hypertext transfer protocol; this is a protocol responsible for correct transfer of files that make up web pages on the world wide web |
| SMTP | simple mail transfer protocol; this handles the sending of emails |
| POP3/4 | post office protocol; this handles the receiving of emails |
| IMAP | internet message access protocol; this handles the receiving of emails |
| DNS | domain name service; protocol used to find the IP address, for example when sending emails |
| ETP | file transfer protocol; this is a protocol used when transferring messages and attachments |
| RIP | routing information protocol; this is the protocol routers use to exchange routing information over an IP network |
| SNMP | simple network management protocol; protocol used when exchanging network management information between network management and network devices (such as routers, servers and other network devices) |
Hypertext transfer protocol (HTTP)
- HTTP is probably the most important application layer protocol.
- Essentially, this protocol underpins the world wide web.
- It is used when, for example, fetching an HTML document from a web server.
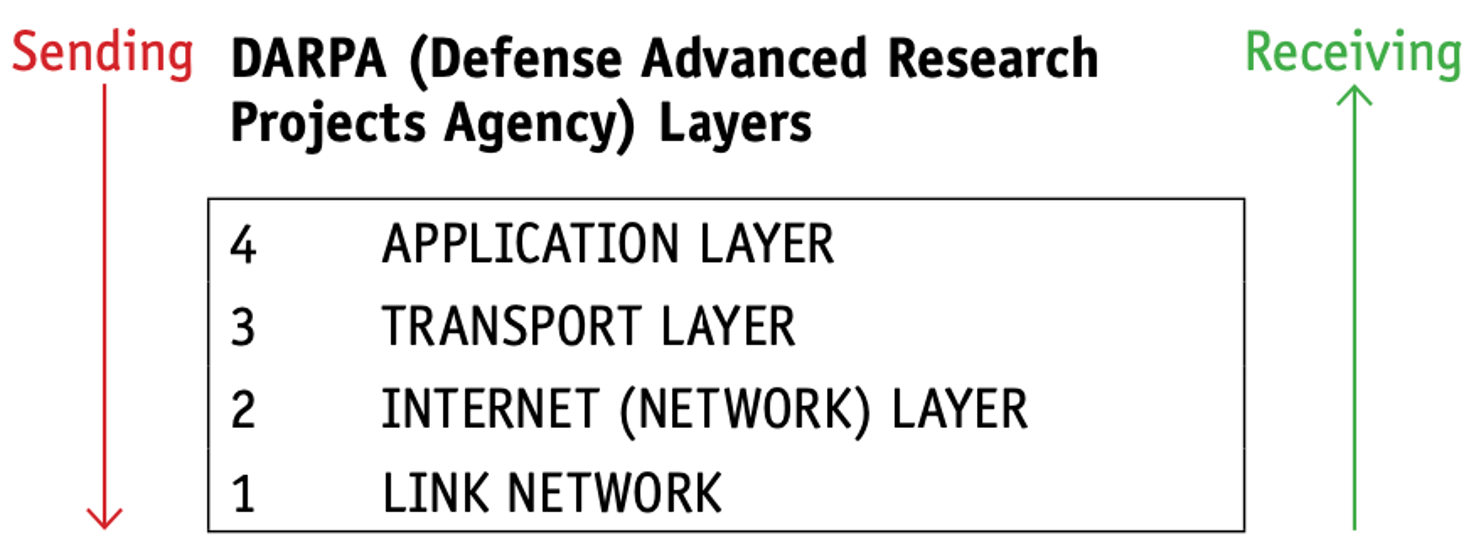
what happens when a user requests a web page from a website?
- The user keys the URL into their browser.
- HTTP(s) transmits the request from the application layer to the transport layer (TCP).
- The TCP creates data packets and sends them (via port 80) to the destination port(s).
- The DNS server stores a database of URLs and matching IP addresses.
- The DNS server uses the domain name typed into the browser to look up the IP address of the appropriate website.
- The server TCP sends back an acknowledgement (see the section on host-to-host communication on page 333).
- Once communication has been established, the web server sends the web page back in HTML format to the browser.
- The browser interprets the page and displays it or sends the data in the correct format to the media player.
File transfer protocol (FTP)
The file transfer protocol (FTP) is a network protocol used when transferring files from one computer/device to another via the internet or other networks.
It is similar to HTTP and SMTP, but FTP’s only task is the application protocol for the transfer of files over a network. - - FTP example,
ftp://username@ftp.example.gov/Additional features of FTP include
- anonymous ftp – this allows a user to access files without the need to identify who they are to the ftp server;
- ftp commands – a user is able to carry out actions that can change files stored on the ftp server; for example, delete, close, rename, cd
- ftp server – this is where the files, which can be downloaded as required by a user, are stored.
Simple mail transfer protocol (SMTP)
- Simple mail transfer protocol (SMTP) is a text-based (and connection-based) protocol used when sending emails.
- It is sometimes referred to as a push protocol (in other words, a client opens a connection to a server and keeps the connection active all the time; the client then uploads a new email to the server).
- Since SMTP is text-based only, it doesn’t handle binary files (a binary file is a file containing media/images as well as text and is regarded as being computer- readable only).
- If an email contains attachments made up of, for example, images, video, music then it is necessary to use the multi-purpose internet mail extension (MIME) protocol instead.
- A MIME header is used at the beginning of the transmission; clients use this header to select which media player is needed when the attachment is opened.
POP3/4 and IMAP (post office protocol and internet message access protocol)
- Post office protocol (POP3/4) and internet message access protocol (IMAP) are protocols used when receiving emails from the email server.
- These are known as pull protocols (the client periodically connects to a server; checks for and downloads new emails from the server – the connection is then closed; this process is repeated to ensure the client is updated).
- IMAP is a more a recent protocol than POP3/4, but both have really been superseded by the increasing use of HTTP protocols. - However, SMTP is still used when transferring emails between email servers.

- The main difference between POP3/4 and IMAP is synchronisation
| POP3/4 | IMAP |
|---|---|
| POP3/4 does not keep the server andclient in synchronisation: when emails aredownloaded by the client, they are thendeleted from the server which means it isnot further updated. | IMAP keeps the server and client insynchronisation; only a copy of the emailis downloaded with the original remainingon the server until the client manuallydeletes it. |
Transport layer
- The transport layer regulates the network connections; this is where data is broken up into packets which are then sent to the internet/network layer (IP protocol).
- The transport layer ensures that packets arrive in sequence, without errors, by swapping acknowledgements and retransmitting packets if they become lost or corrupted.
- The main protocols associated with the transport layer are transmission control protocol (TCP), user datagram protocol (UDP) and SCTP. We will only consider TCP.
Transmission control protocol (TCP)
- TCP is responsible for the safe delivery of a message by creating sufficient packets for transmission.
- It uses positive acknowledgement with re- transmission (PAR) which means it automatically re-sends a data packet if it has not received a positive acknowledgement.
- TCP is also connection- orientated since it establishes an end-to-end connection between two host computers using handshakes.
- For this last reason, TCP is often referred to as a host-to-host transmission protocol.
- The term host has been used previously; this refers to a computer or device that can communicate with another computer/device (host).
- Hosts can include clients and servers that send/receive data, provide services or apps.
Internet/network layer and network/data-link layer
- The internet layer identifies the intended network and host.
- The common protocol is IP (internet protocol).
- The concept of IPv4 and IPv6 was covered in depth in Chapter 2.
- The network/data-link layer identifies and moves traffic across local segments, encapsulates IP packets into frames for transmission, maps IP addresses to MAC (physical) addresses and ensures correct protocols are followed.
- The physical network layer specifies requirements of the hardware to be used for the network.
- The data-link layer identifies network protocols in the packet header (TCP/IP in the case here) and delivers packets to the network.
This is a summary of the IP functions
- Ensure correct routing of packets of data over the internet/network.
- Responsible for protocols when communicating between networks.
- Take a packet from the transport layer and add its own header which will include the IP addresses of both sender and recipient.
- The IP packet (datagram) is sent to the data-link layer where it is assembles the datagrams into frames for transmission.
Ethernet protocols
- Ethernet is a system that connects a number of computers or devices together to form a LAN.
- It uses protocols to control the movement of frames between computers or devices and to avoid simultaneous transmission by two or more devices.
- It is a local protocol and does not provide any means to communicate with external devices; this requires the use of IP which sits on top of the Ethernet protocol.
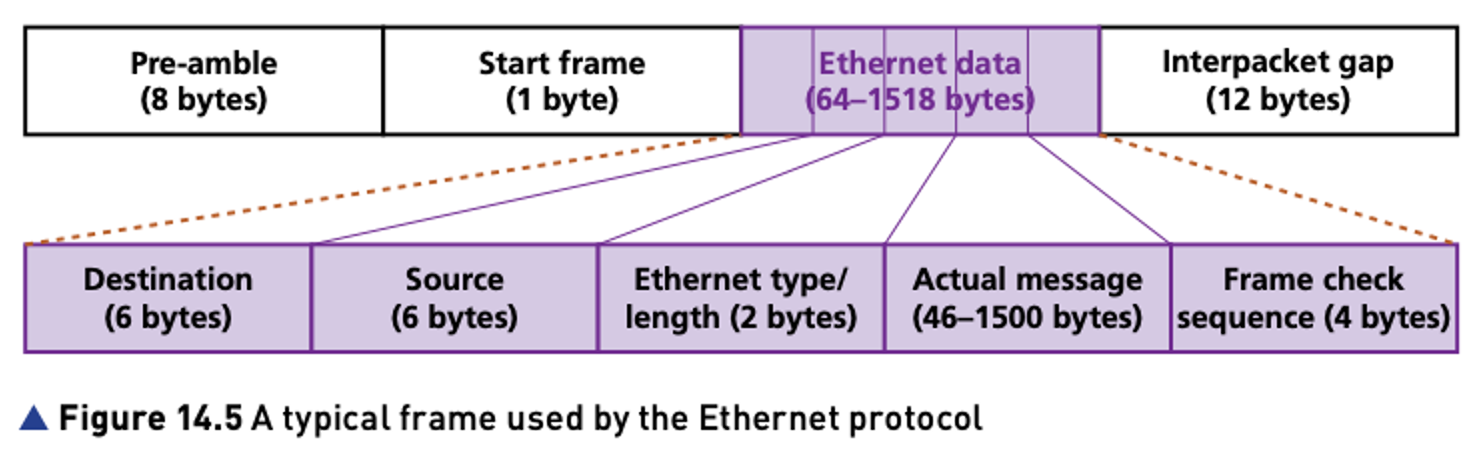
- The components that make up Ethernet data are
- destination – this is the MAC address of the destination computer or device (it is possible to use the value FF:FF:FF:FF:FF:FF as the MAC address if the sender wishes to target every device (for example, to advertise services) or if they do not know the MAC address of the destination device)
- source – this is the MAC address of the source computer (using the usual MAC address format of 6bytes)
- Ethernet type or length – if the frame length ≤ 1539 then the value here is the length of the Ethernet frame; if the frame length > 1539 then the value here is the Ethernet type (IPv4 or IPv6 in our example)
- frame check – this will include a checksum to provide a method of checking data integrity following transmission of the frame.
Wireless (WiFi) protocols
- Wireless LANs (standard IEEE 802.11 protocol) use a MAC protocol called carrier sense multiple access with collision avoidance (CSMA/CA) (not to be confused with CSMA/CD considered in Chapter 2, since this is a totally different concept).
- CSMA/CA uses distributed control function (DCF) to ensure a WiFi device can only transmit when there is a free channel available.
- Since all transmissions are acknowledged when using DCF, if a device does not receive an acknowledgement it will assume a collision will occur and waits for a random time interval before trying again.
- This is an important protocol to ensure the security and integrity of data being sent over a wireless network (such as WLAN).
Bluetooth protocols
- Bluetooth was considered in Chapter 2; it uses the standard IEEE 802.15 protocol for short-range data transmission/communication.
- There are numerous additional Bluetooth protocols due to the many applications that may use this wireless connectivity; this is outside the scope of this textbook.
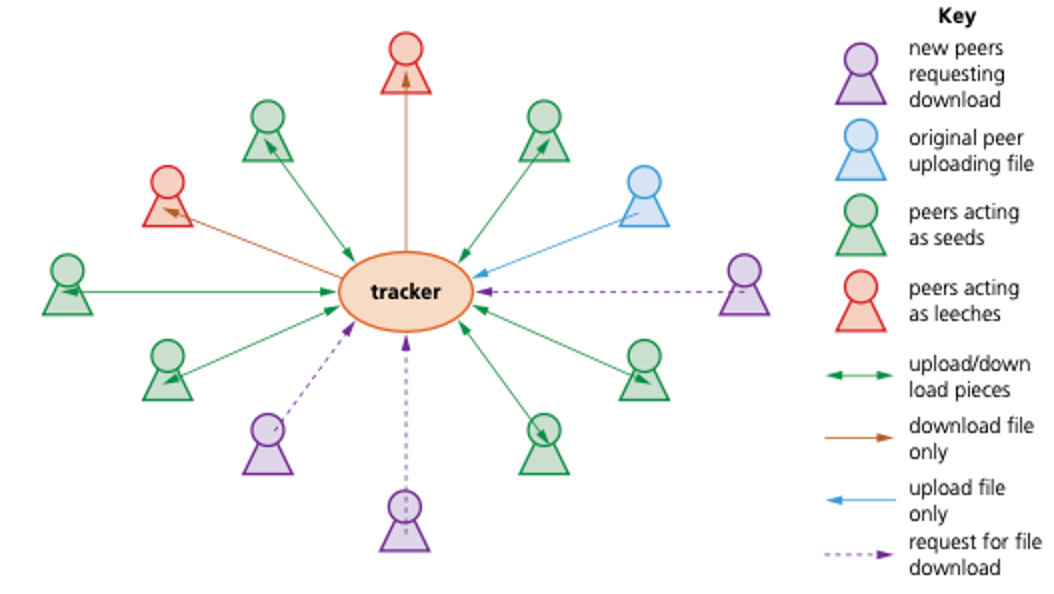
Peer-to-peer file sharing/BitTorrent protocol
- The BitTorrent is a protocol which is based on the peer-to-peer networking concept.
- This allows for very fast sharing of files between computers (known as peers).
- While peer-to-peer networks only work well with very small numbers of computers, the concept of sharing files using BitTorrent can be used by thousands of users who connect together over the internet.
Peer-to-peer
- Metadata – a set of data that describes and gives information about other data.
- Pieces – splitting up of a file when using peer-to-peer file sharing.
- Tracker – central server that stores details of all other computers in the swarm.
- Swarm – connected peers (clients) that share a torrent/tracker.
- Seed – a peer that has downloaded a file (or pieces of a file) and has then made it available to other peers in the swarm.
- Leech – a peer with negative feedback from swarm members.
- Lurker – user/client that downloads files but does not supply any new content to the community.